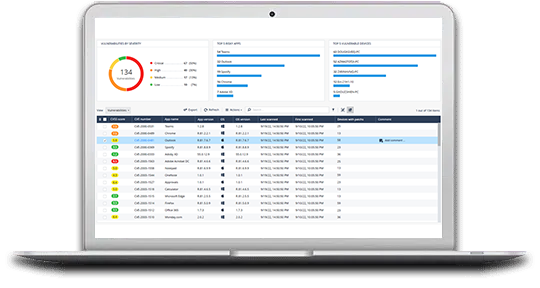
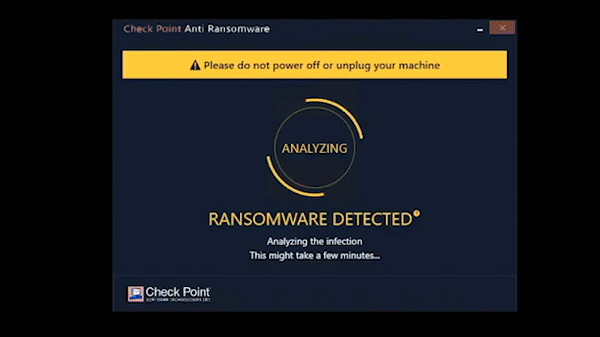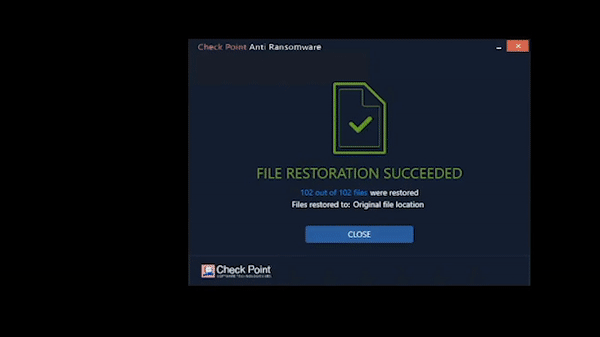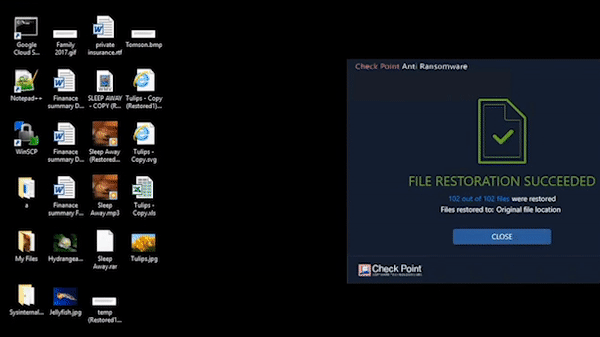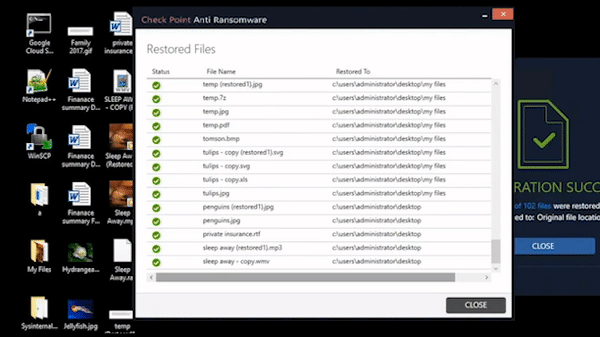
Harmony Endpoint identifies ransomware behaviors such as file-encryption or attempts to compromise operating system backups, and safely restores ransomware-encrypted files automatically.
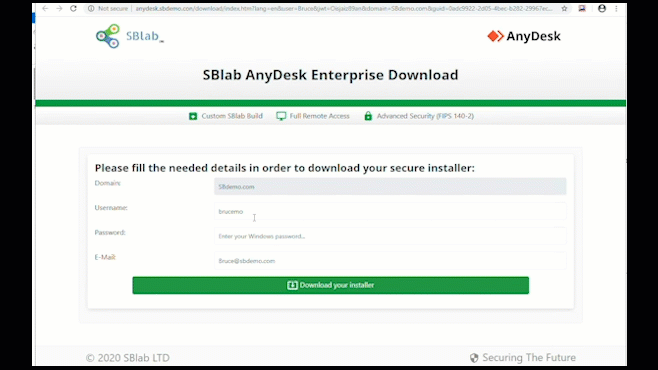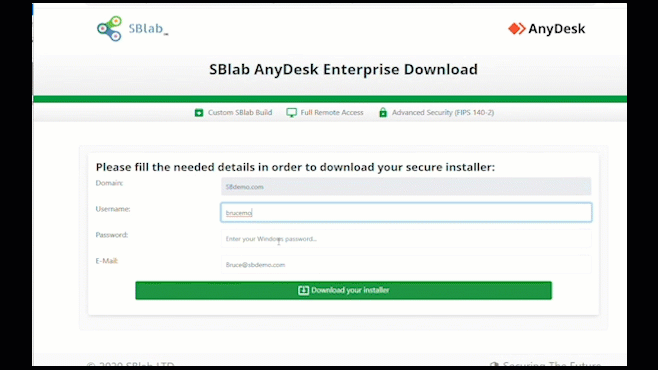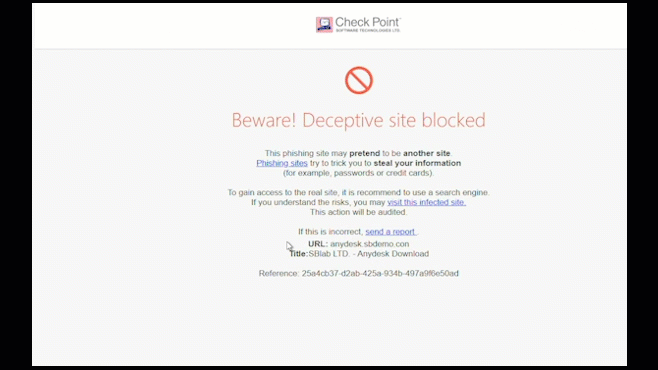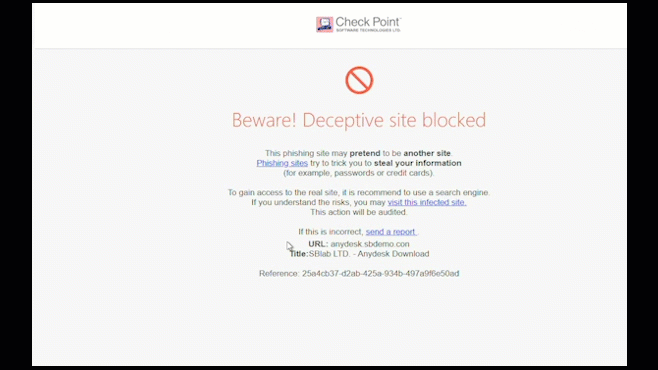
Zero-Phishing technology identifies and blocks the use of phishing sites in real time. Sites are inspected and if found malicious, the user is blocked from entering credentials.
Zero-phishing also protects against previously unknown phishing sites.
Block malware coming from web browsing or email attachments, before it reaches the endpoint, without impacting user productivity.
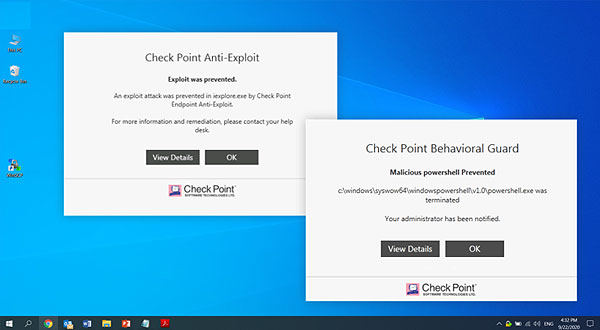
Endpoint Behavioral Guard identifies malware families, file-less attacks, and other generic malicious behavior.
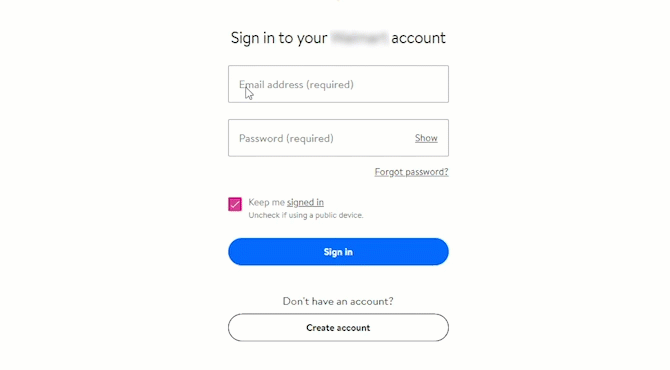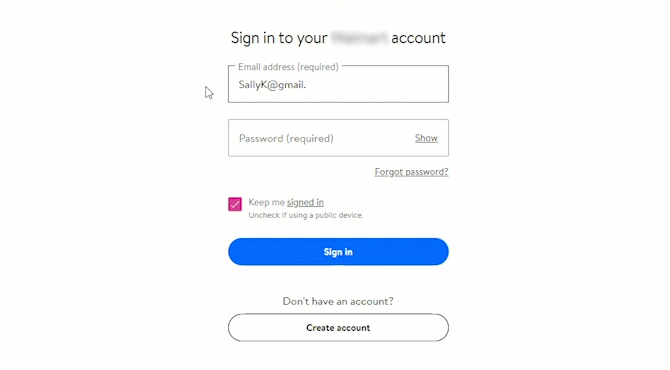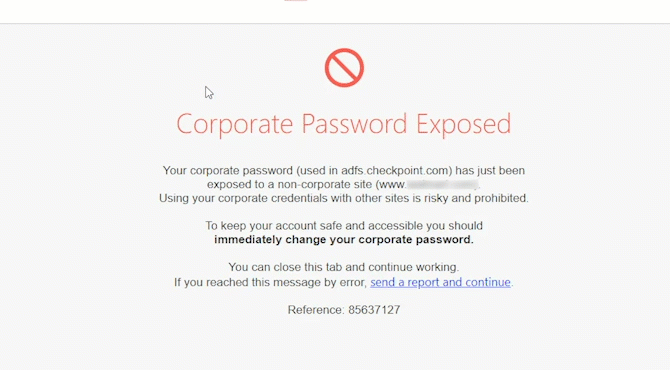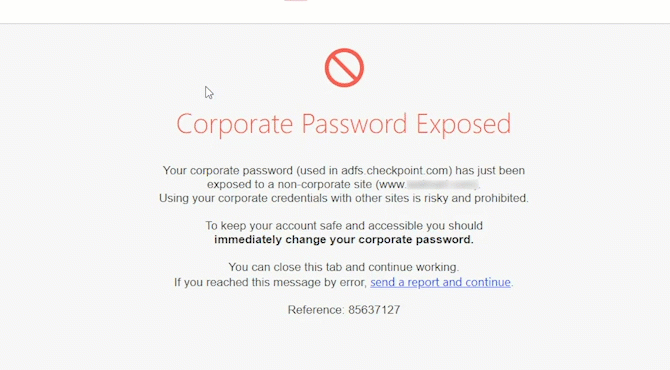
Preventing credential theft and corporate credential re-use.
Every file received via email or downloaded by a user through a web browser is sent to the Threat Emulation sandbox to inspect for malware.
Files are also sanitized using a Threat Extraction process (Content Disarm & Reconstruction technology) to deliver sanitized content in milliseconds.